2018 Practice Test
Got nothing, moreorless a reminder for myself.
Scoring
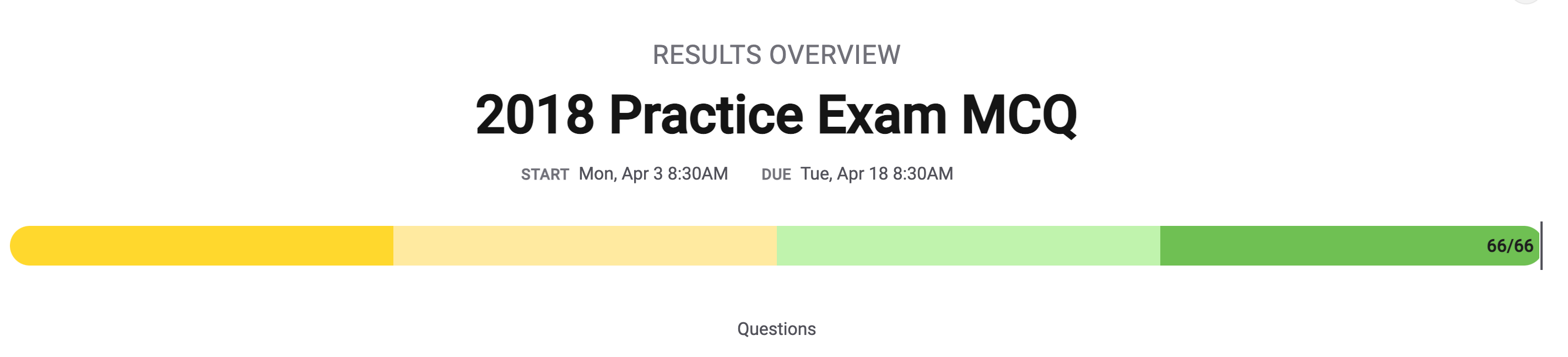
As you can see, I actually got a full score on this review. However, it was definitely challenging, so I wanted to go over some questions that I thought were extremely challenging or confusing so I have a better time tackling the actual exam when the time comes.
Q64: Cloud Computing - Cloud computing allows for enhanced collaboration - Introduces new data-security concerns with the addition of better access to others - CLOUD COMPUTING HAS NOTHING TO DO WITH IPRs, so do not mention it in the exam. I had a lot of trouble between C and D because of this.
Q51: Which of the Following demonstrates symmetric encryption?
-
Symmetric encryption is a type of encryption algorithm that uses a single key for both encryption and decryption. In other words, the same key is used to both scramble (encrypt) and unscramble (decrypt) the data. This means that the same key is shared between the sender and the receiver of the encrypted data.
-
The process of symmetric encryption typically involves the following steps:
-
Key Generation: A single key is generated by the sender, and this key is used for both encryption and decryption.
-
Encryption: The sender uses the key and an encryption algorithm to scramble the plain text data into cipher text. The cipher text is the result of applying the encryption algorithm to the plain text using the key, making it unreadable without the key.
-
Transmission: The cipher text is transmitted over a secure channel to the receiver.
-
Decryption: The receiver uses the same key and the same encryption algorithm to apply the reverse process, transforming the cipher text back into the original plain text.
-
-
One key advantage of symmetric encryption is its speed and efficiency, as it requires less computational power compared to other types of encryption like asymmetric encryption. However, a significant challenge with symmetric encryption is securely sharing the secret key between the sender and the receiver. Any compromise of the key can result in the unauthorized access to the encrypted data.
-
To maintain the confidentiality and security of symmetric encryption, it is essential to use secure key management practices, such as securely distributing and storing the key, changing the key periodically, and limiting access to the key only to authorized parties.
-
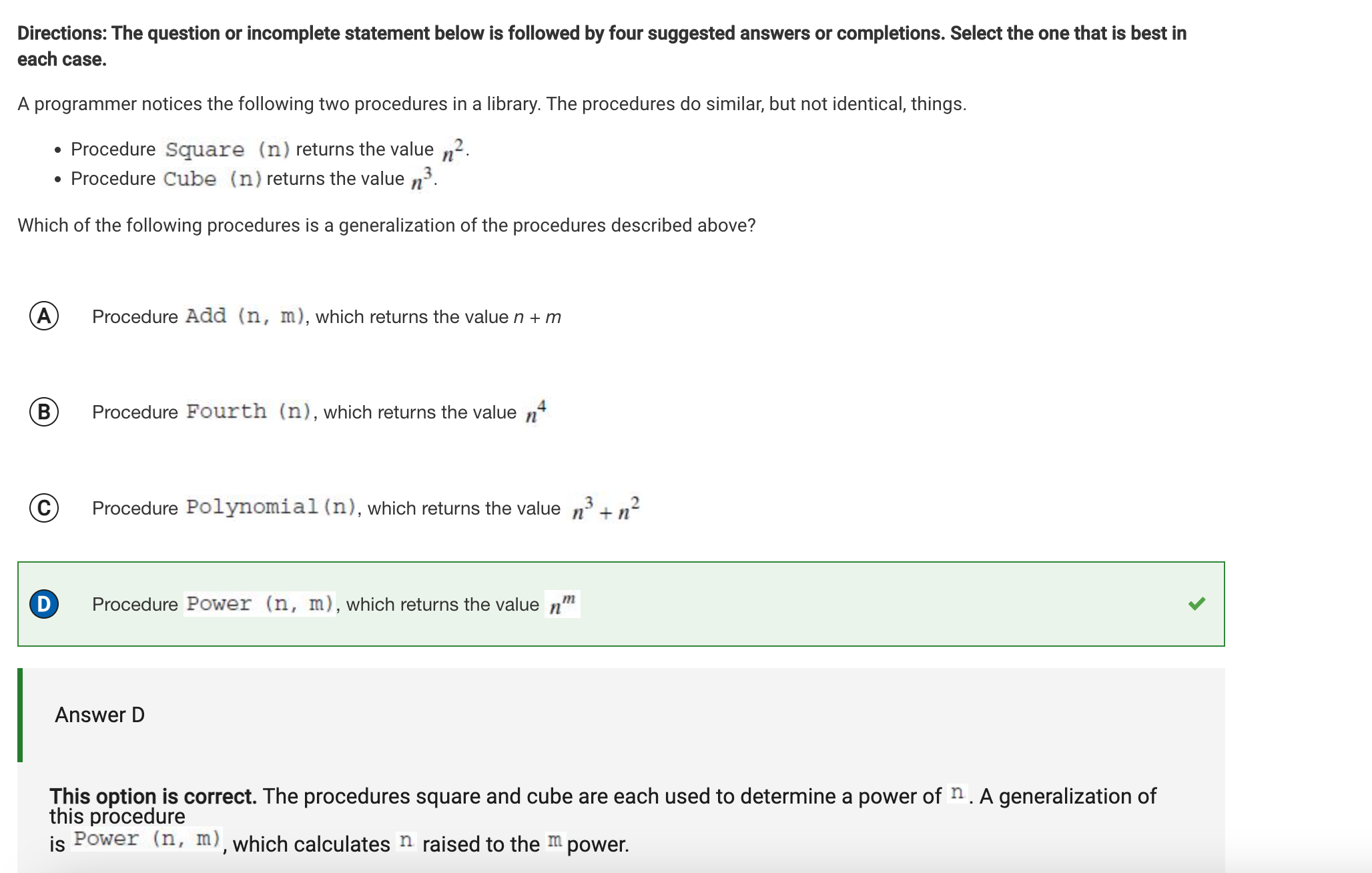
Q54 Abstraction
Q9
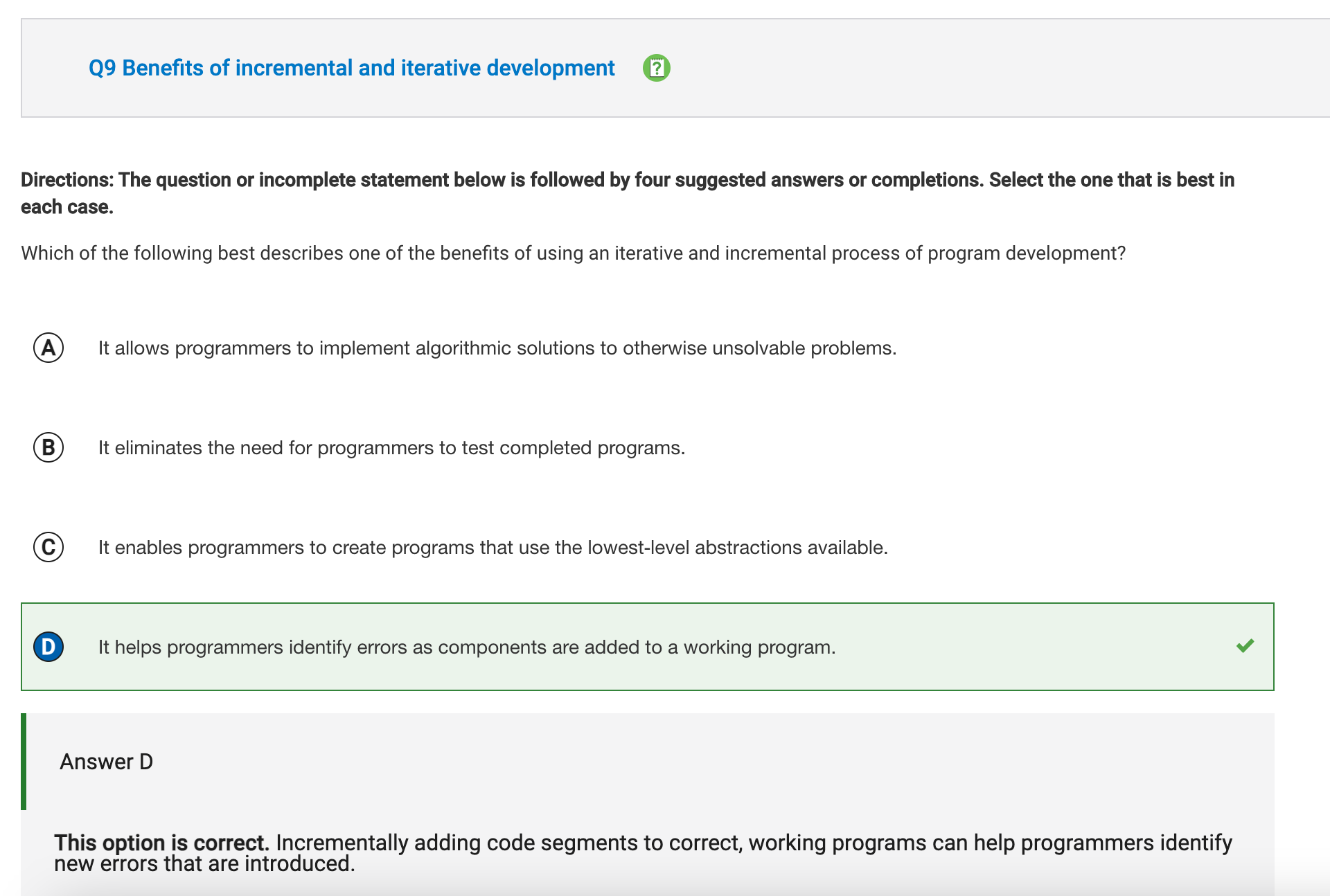
Overall, the test was not too challenging and only took me roughly an hour and fifteen minutes to finish. These were just some of the questions that caught me off guard and will need further preparation so that I am more comfortable taking the exam in May